Understanding KnowX and Their Data Brokering Practices - A Comprehensi…
페이지 정보

본문
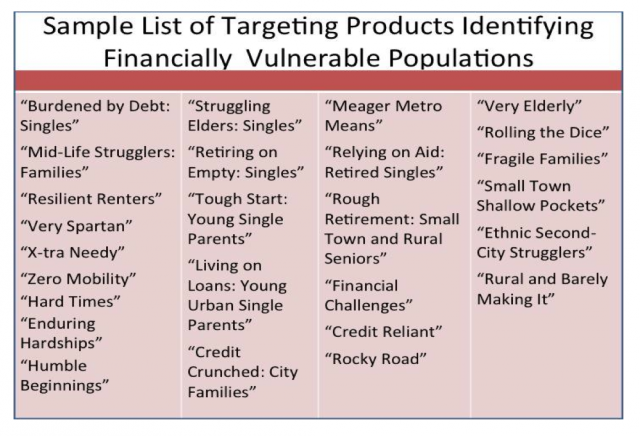
In today's digital landscape, the intricate web of information exchange plays a vital role. Individuals often find themselves navigating a myriad of services that rely on personal insights. It can be fascinating yet overwhelming. Such platforms promise convenience but often come with hidden intricacies. Probing deeper into these systems reveals a blend of transparency and opacity.
Understanding how these entities operate is essential for informed decision-making. Users frequently seek to know what personal details are being shared. The level of awareness varies widely from one person to another. This lack of knowledge creates gaps in user experience and trust. Consequently, a thorough examination of the underlying mechanisms is imperative.
Numerous factors influence how personal information is collected, utilized, and disseminated. The technology that facilitates these exchanges is rapidly evolving. As innovations emerge, understanding the implications becomes increasingly critical. This dynamic environment requires careful scrutiny, especially regarding privacy considerations and ethical concerns.
By diving into the specifics of these operations, one can unveil the nuances that define them. Many may be unaware of the extent of information that circulates about them. What is particularly striking is the reality that the value of such insights often goes unnoticed. Ultimately, fostering awareness can empower individuals in this complex ecosystem.
Understanding Data Brokers
In today's digital landscape, the collection and utilization of personal information have become increasingly prevalent. There exists a multitude of entities specializing in the acquisition, aggregation, and dissemination of consumer details for various purposes. These organizations operate in a complex web of privacy, consent, and profit, often without individuals realizing the extent of their activities. The sheer volume of information available can be staggering. Most people are not aware that their data is actively being bought and sold.
The services provided by these organizations can be categorized into several key areas:
- Information aggregation
- Consumer profiling
- Marketing services
- Risk management for businesses
Understanding the intricacies of these operations is crucial for consumers hoping to protect their privacy. Each entity has its methods for collecting data, which can vary widely. While some sources are reputable, others may engage in questionable practices.
These firms often gather information from a variety of channels, including public records, surveys, and online activities. For example, social media platforms provide a wealth of personal insights that are frequently exploited. By analyzing trends, preferences, and behaviors, these organizations create comprehensive profiles that can be sold to marketers, businesses, or even government agencies.
Moreover, the ethical implications cannot be overstated. Many individuals remain unaware of how their information is handled, leading to potential misuse. The lack of transparency surrounding these operations raises significant concerns. Thus, knowledge and awareness are essential for navigating this complex ecosystem.
As consumers, it is our responsibility to educate ourselves about the mechanisms at play. Being informed is the first step toward safeguarding our personal information. Recognizing how these entities operate empowers us to make better decisions regarding our privacy.
What is KnowX?
In today’s interconnected world, the collection of information has become paramount. Various platforms utilize a multitude of techniques to gather personal details. This section will delve into the methods employed to acquire such information, shedding light on the sophistication and variety involved.
Understanding how information is collected can help individuals navigate this complex landscape. Not all techniques are the same. Some are transparent, while others operate in the shadows. The technologies range from advanced software to traditional means of gathering insights.
- Online Tracking: Many entities employ cookies and tracking pixels to monitor user behavior. This method allows them to gather data on browsing habits, preferences, and interests.
- Public Records: Accessing governmental and legal documents can yield a wealth of personal information. These records are often freely available and can include everything from property ownership to legal filings.
- Surveys and Questionnaires: Engaging with individuals directly through surveys can provide valuable insights. Incentivizing participation often results in a higher response rate.
- Social Media Scraping: By analyzing profiles, posts, and interactions, platforms can extract substantial amounts of information for various uses.
- Purchasing Data: Many organizations opt to buy information from third-party sources. This allows for quick access to already compiled databases of personal details.
These techniques, while diverse, share the common goal of accumulating information that can be used for various purposes, from targeted advertising to market research. The implications of such practices can be significant, impacting personal privacy and influencing how companies interact with individuals.
As technology continues to evolve, so too do the methods of collecting personal information. Understanding these approaches is essential for anyone seeking to safeguard their privacy in an increasingly digital age.
Data Collection Methods Explained
In today's interconnected world, the acquisition of user information has become an intricate process. Various entities employ a multitude of techniques to gather insights about individuals. This range encompasses anything from voluntary submissions to clandestine tracking. It is essential to comprehend these methods to understand the broader implications on personal privacy. Consumers often remain unaware of how their information is utilized.
One prevalent method involves online tracking through cookies. These small snippets of data, stored on a user’s device, allow entities to monitor browsing habits. By analyzing that information, companies can refine their marketing strategies. Additionally, surveys and questionnaires represent another avenue. Users may provide personal insights in exchange for incentives, such as discounts or sweepstakes entries. This strategy can yield rich datasets, revealing user preferences and behaviors.
Another common approach is public records analysis. Publicly accessible information, like voter registrations or property records, can be compiled and processed. By cross-referencing various sources, entities can create detailed profiles of individuals. This method often goes unnoticed, leading consumers to believe their information remains private. Moreover, social media platforms contribute significantly to data accumulation. When individuals share updates, posts, and personal details, they inadvertently enrich the existing pool of data.
In addition, mobile applications frequently collect user information via permissions. Many apps request access to contacts, location, and more, often without full transparency. These permissions can lead to extensive user profiling. Mobile tracking might also be achieved through GPS, enabling real-time location monitoring. Such methods collect vast amounts of data, which can be analyzed to identify trends and behaviors.
Lastly, third-party partnerships play a crucial role. Companies often collaborate with external organizations to obtain additional insights. This symbiotic relationship allows for the sharing and selling of information across platforms. It creates a vast network of data exchange that can be immensely valuable for targeted advertising. While this approach may seem beneficial to businesses, it raises significant concerns regarding consumer privacy and consent.
Types of Data Acquired by KnowX
The landscape of information gathering is vast and diverse. Various entities collect a myriad of details for different purposes. This section delves into the specific types of information that are commonly obtained. The nature of this data can significantly impact individuals' privacy and security. Let’s explore the kinds of details that can be collected.
Personal Identifiable Information (PII) is one of the primary categories. This includes names, addresses, and phone numbers. Such details allow for the identification of individuals. Additionally, demographic data such as age, gender, and ethnicity can also be included. These insights are often used for targeting specific audiences in marketing campaigns.
Another significant group is financial records. It encompasses credit scores, transaction histories, and even bank account information. These financial details can be extremely sensitive. They are often sought after for purposes like assessing creditworthiness or identifying potential clients. Thus, gaining access to this information poses both risks and benefits.
Moreover, online behavior is increasingly being tracked and documented. This refers to users' activities across websites and platforms. Browsing habits, purchase records, and social media interactions are all included within this category. This wealth of information allows for creating detailed consumer profiles. In turn, it feeds into targeted advertising and customized offerings that are designed to entice potential customers.
Additionally, location data is being harvested through various technologies. GPS signals from smartphones and location tracking from applications are common. This type of information is particularly valuable for businesses that rely on geographical insights. Knowing where a consumer frequently visits can enhance localized marketing strategies, yet it raises serious concerns regarding privacy and personal freedom.
Lastly, there’s a growing interest in public records. These documents include court records, property ownership, and professional licenses. They provide a comprehensive view of an individual's history and affiliations. While these records are often accessible to the public, the way they are compiled and utilized must be examined carefully to ensure ethical practices.
In conclusion, the types of information gathered by various entities are extensive and multifaceted. Understanding these categories is crucial for individuals concerned about their privacy. By being aware of what information is collected, individuals can better protect their personal data and make informed decisions about engaging with different services.
Privacy Concerns with Data Brokers
The collection and utilization of personal information have become a prominent issue in today's society. Individuals often find themselves in a complex web of data exchange without their explicit consent. Concerns about transparency and security grow as more entities engage in amassing vast troves of private details. This lack of awareness leads to a diminished sense of control over one's own information. Moreover, the implications of such practices can be far-reaching, impacting everything from personal security to social interactions.
Many people may not realize the extent to which personal information can be harvested. With an array of sophisticated techniques, organizations can compile comprehensive profiles. These profiles often include sensitive details like income levels, purchasing habits, and even medical history. It’s alarming to think that such intimate data can be bought and sold without individuals having any say in the matter.
Furthermore, there is a troubling irony in the promises of technology designed to enhance privacy. While it ostensibly aims to protect identities, it inadvertently fuels the very industries that compromise them. The question of who is ultimately responsible for safeguarding this information looms large. Without stringent regulations, the ethical implications of such practices can easily be overlooked.
In light of these concerns, individuals must advocate for greater accountability from entities involved in collecting personal details. Many might feel powerless, but awareness is the first step toward change. Understanding how information is used–and sometimes misused–can empower consumers to take necessary precautions. As more people become informed, the demand for robust privacy measures may compel organizations to reconsider their operations.
The risks associated with mismanagement of personal data cannot be underestimated. Identity theft is just one of the harmful consequences that can result from negligence in handling sensitive information. Even seemingly harmless data can contribute to larger patterns of exploitation. For example, when combined with other sources, even benign details can lead to unwanted harassment or targeted scams.
Ultimately, as society progresses into an increasingly digital age, the balance between convenience and privacy requires careful examination. Addressing these concerns is not just about protecting oneself; it’s about fostering a culture of respect and responsibility regarding personal information. Everyone deserves to have control over what is shared and how it is utilized. We must strive for a future where privacy is paramount, not an afterthought.
KnowX’s Compliance with Laws
Ensuring adherence to legal standards is essential for any organization involved in information collection. Compliance not only builds trust but also protects the rights of individuals. For those operating in the realm of consumer information, understanding various regulations is crucial. Regulations can vary significantly depending on the jurisdiction. Moreover, these laws evolve over time, demanding constant vigilance.
Organizations must navigate a complex landscape of legal obligations. This includes everything from data protection to consumer privacy rights. For instance, entities must often comply with regulations like the General Data Protection Regulation (GDPR) in Europe or the California Consumer Privacy Act (CCPA) in the United States. Each of these frameworks outlines specific requirements for transparency, user consent, and data security.
| Regulation | Region | Key Requirements |
|---|---|---|
| General Data Protection Regulation (GDPR) | European Union | Informed consent, data access, and deletion rights |
| California Consumer Privacy Act (CCPA) | California, USA | Disclosure, opt-out, and data deletion rights |
| Health Insurance Portability and Accountability Act (HIPAA) | USA | Protection of health information and patient privacy |
Organizations engaged in information collection must take these regulations very seriously. Non-compliance can result in hefty fines and significant reputational damage. Therefore, continuous training and awareness programs for employees are vital. Companies often establish dedicated teams to monitor evolving regulations and ensure adherence. This proactive approach not only mitigates risks but also fosters a culture of accountability and respect for consumer rights.
Transparency is another key element of compliance. Clear communication regarding how information is collected, used, and shared is essential. It helps consumers make informed choices. In addition, companies often provide accessible methods for individuals to manage their personal information. This includes options for deletion or opting out of information sharing.
Ultimately, the focus on legal compliance reflects a broader commitment to ethical practices. Organizations in this field must prioritize respect for individual privacy. By doing so, they not only protect themselves legally but also build lasting relationships with consumers based on trust. The evolving nature of privacy laws means that maintaining compliance is an ongoing challenge, yet it is one that can yield significant benefits.
How KnowX Uses Collected Data
The utilization of acquired information plays a crucial role in various sectors. Knowing how this information is leveraged can illuminate the impact on personal privacy. Organizations often harness collected data to enhance their services, tailor marketing, or predict consumer behavior. It is fascinating yet concerning how individuals' details can influence these decisions. Moreover, the methods of application can vary widely, depending on the goals of the organization.
Primarily, information is used for marketing purposes. Businesses aim to create targeted advertising campaigns that resonate with specific audiences. By analyzing user behavior, preferences, and demographics, they develop strategies that maximize engagement. This targeted approach can significantly increase conversion rates. However, it also raises questions about consent and individual privacy.
Furthermore, the aggregated data can serve analytical purposes. Companies may employ it to assess market trends or consumer needs. Such insights can drive decision-making processes and lead to more informed business strategies. Collectively, this information can help organizations stay competitive in an ever-evolving market landscape.
Another application involves risk assessment and fraud detection. Financial institutions and services utilize detailed profiles to evaluate creditworthiness. By analyzing historical behavior, they can identify potential risks associated with lending or other transactions. This practice is essential for minimizing losses and protecting both the business and its customers.
In summary, the ways in which collected information is employed are diverse and multifaceted. It can facilitate marketing strategies, analytical pursuits, and risk management practices. However, the implications for privacy remain significant. Users must be aware of how their information is utilized and the potential consequences. It raises critical questions about the balance between business interests and individual rights.
| Use of Information | Description |
|---|---|
| Marketing | Create targeted campaigns based on consumer behavior and preferences. |
| Analytics | Assess market trends and consumer needs for informed decision-making. |
| Risk Assessment | Evaluate creditworthiness and fraud detection in financial transactions. |
Consumer Rights and Data Access
In today’s digital age, individuals have the right to know what information is collected about them. Understanding these rights is essential for maintaining privacy and ensuring control over personal information. Many people are unaware of the extent to which their details are stored and shared. It's crucial to be informed about how to access this information and what options are available for rectifying inaccuracies.
The ability to review one's information empowers consumers. A person can not only see what is held but can also challenge incorrect data. This process is often more straightforward than it seems. However, the steps to gain this access may vary widely depending on the source of the information. Each organization often has its own protocols, which may lead to confusion.
Furthermore, in many regions, there are regulations in place that enforce transparency. These laws require entities to provide access upon request, thus enabling individuals to understand what is being shared. The framework often includes timelines for responses and may stipulate specific forms of identification to verify requests.
In practice, engaging with such organizations can sometimes feel overwhelming. It’s advisable to keep detailed records of all communications. Being persistent can lead to better outcomes when seeking your information. Additionally, knowing your rights equips you to navigate the complexities of accessing data effectively.
Ultimately, vigilance is necessary to safeguard personal privacy. By actively seeking access and correcting inaccuracies, individuals can help protect themselves from unwanted exposure. Knowledge is power; understanding rights ensures that one can effectively assert control over personal information.
Steps to Remove Your Information
In an era where personal details are collected and sold, protecting your privacy has become paramount. Many individuals are unaware of how widespread this practice is. It can feel overwhelming to navigate the process of having your information erased. Yet, taking action to safeguard your personal data is essential. Fortunately, there are avenues available for you to reclaim your privacy.
First, it’s crucial to identify the sources that may hold your information. Some companies specialize in gathering and distributing personal details. Researching these organizations is a significant step. Once you know where to look, you can reach out to them directly.
Next, gather any necessary documentation. You might need identification or proof of residence. This information helps verify your identity during the removal process. Be prepared to submit requests according to each organization’s unique requirements.
Many companies provide online forms for Medium removal requests, which can simplify the process. Typically, you'll fill out a form with your details and specify what you want to be removed. This is often the fastest method. Alternatively, some firms may require written requests sent via mail.
When sending requests, ensure you keep copies for your records. It’s advisable to track your correspondence as well. This tracking will provide evidence of your efforts should any disputes arise in the future. Additionally, follow up if you do not receive a prompt confirmation of your request.
To further facilitate the process, here’s a helpful overview of steps you may take:
| Step | Description |
|---|---|
| Identify Sources | Find out which companies may have your information. |
| Document Preparation | Gather necessary documents for identity verification. |
| Submit Requests | Fill out online forms or send written requests. |
| Keep Copies | Retain records of your requests for future reference. |
| Follow Up | Check back with companies if you don’t receive confirmation. |
Finally, it’s important to stay vigilant. Regularly monitor your online presence and utilize tools for protecting your privacy. By being proactive, you can ensure your personal information remains secure in an increasingly invasive digital world. Remember, your privacy is your right, and taking these steps can help you maintain control over your personal data.
Alternatives to Data Broker Services
In today's digital landscape, individuals are increasingly concerned about privacy and the usage of personal information. Many people are searching for options that allow them to regain control over their own data. Thankfully, there are several alternatives available that can help minimize unwanted exposure. These solutions vary from user-controlled settings to various platforms prioritizing privacy. By exploring these alternatives, you can empower yourself and make informed choices.
One option is utilizing privacy-focused search engines. Unlike traditional search engines, these platforms prioritize user anonymity and do not track searching habits. Examples include DuckDuckGo and Startpage, which provide users with search results without the collection of personal data. This approach can significantly reduce the footprint left behind during online searches.
Another effective strategy is using Virtual Private Networks (VPNs). A VPN encrypts your internet connection, masking your IP address. This adds a layer of security and privacy, making it harder for others to track your online activities. Moreover, VPNs can help access region-restricted content, allowing users to surf the web freely.
Social media users can also consider alternative platforms. Instead of mainstream networks, options like MeWe and Minds offer smaller, privacy-centric communities. These sites often have minimal advertising and greater transparency regarding user data utilization. Users can engage with friends and share content without the pervasive surveillance typically seen on larger platforms.
For those concerned about personal information management, data privacy tools like privacy dashboards or browser extensions can be quite beneficial. These tools help manage what data is shared and can block trackers from gathering information while you browse. Implementing these measures provides greater control over online activity, significantly enhancing personal security.
Lastly, one can adopt a more mindful approach to online sharing. By being selective about the information shared on websites, users can significantly reduce their digital footprint. Regularly reviewing privacy settings and adjusting them based on preferences is crucial. An informed user can make choices that align with their comfort levels regarding privacy.
In conclusion, while traditional avenues may expose individuals to unwanted scrutiny, a variety of effective alternatives exist. Exploring privacy-focused search engines, utilizing VPN services, engaging with privacy-centric social media platforms, employing data privacy tools, and adopting mindful sharing practices can collectively contribute to enhanced personal security. Each alternative offers unique advantages, allowing individuals to navigate the online world with greater confidence.
The Future of Data Brokerage
As technology evolves, the landscape of information exchange continues to shift dramatically. This transformation impacts how private information is collected, accessed, and utilized. New tools and strategies are emerging that not only enhance the efficiency of information gathering but also challenge existing ethical standards. The role of individuals in this ecosystem is becoming increasingly vital, as awareness grows about privacy concerns and individual rights.
Recent trends indicate a movement toward greater transparency in the management of personal information. Consumers are now more informed about how their details are used, prompting a reassessment of traditional practices. Furthermore, regulatory bodies are becoming more engaged, leading to changes that could redefine interactions between individuals and service providers. This raises the question: how will these shifts influence the future?
Advancements in artificial intelligence and machine learning are set to revolutionize operations in this field. These technologies offer unprecedented capabilities for analyzing and predicting consumer behavior. As a result, the methods of information aggregation will become more nuanced, allowing for tailored offerings that were previously unimaginable.
However, this evolution is not without its pitfalls. Ethical dilemmas abound as the boundaries of acceptable use are tested. The growing capability to personalize services raises concerns about surveillance and autonomy. While enhanced personalization can benefit consumers, it can also lead to invasive practices that undermine trust.
Moreover, the emergence of decentralized technologies, such as blockchain, could alter the dynamics profoundly. These innovations promise increased control for individuals over their own information, potentially disrupting established models of information dissemination. The future could see a shift toward models that prioritize consumer agency and informed consent.
The role of legislation will also play a crucial part in shaping the future. As governments worldwide respond to growing public concerns regarding privacy, we can expect more stringent regulations to emerge. These laws may enforce stricter compliance measures, compelling organizations to adapt their strategies to remain viable in an ever-changing regulatory environment.
In conclusion, the trajectory of information exchange appears to be one of increased sophistication and complexity. With rising consumer awareness and technological advancements, the landscape will continue to evolve. How these factors will interact remains to be seen, but one thing is clear: the future will demand new approaches, fresh ideas, and a commitment to ethical standards that prioritize respect for individual rights.
- 이전글10 . Pinterest Account To Be Following About Asbestos Cancer Lawyer Mesothelioma Settlement 24.10.04
- 다음글The Ultimate Glossary Of Terms About Sport Toto Today 24.10.04
댓글목록
등록된 댓글이 없습니다.